- ESET researchers uncovered the Operation RoundPress espionage campaign, with Russia-aligned Sednit group most likely behind it.
- In Operation RoundPress, the compromise vector is a spearphishing email leveraging an XSS vulnerability to inject malicious JavaScript code into the victim’s webmail page. It targets Roundcube, Horde, MDaemon, and Zimbra webmail software.
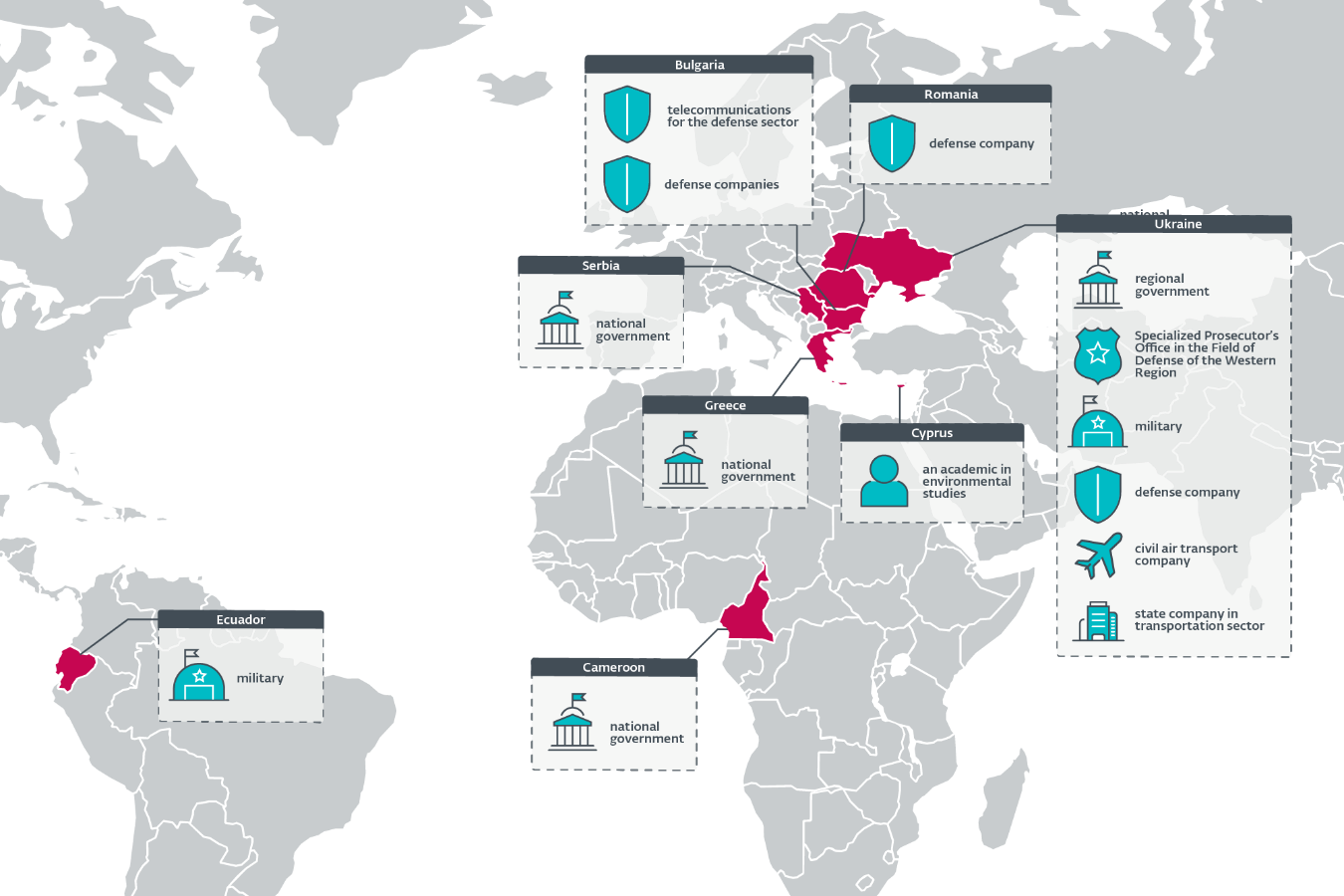
- Most victims are governmental entities and defense companies in Eastern Europe, although ESET has observed governments in Africa, Europe, and South America being targeted as well.
- The payloads are able to steal webmail credentials, and exfiltrate contacts and email messages from the victim’s mailbox.
- Additionally, SpyPress.MDAEMON is able to set up a bypass for two-factor authentication.
MONTREAL and BRATISLAVA, Slovakia, May 20, 2025 (GLOBE NEWSWIRE) — ESET researchers have uncovered a Russia-aligned espionage operation, which ESET named RoundPress, targeting webmail servers via XSS vulnerabilities. Behind it is most likely the Russia-aligned Sednit (also known as Fancy Bear or APT28) cyberespionage group, holding the ultimate goal of stealing confidential data from specific email accounts. Most of the targets are related to the current war in Ukraine; they are either Ukrainian governmental entities or defense companies in Bulgaria and Romania. Notably, some of these defense companies are producing Soviet-era weapons to be sent to Ukraine. Other targets include African, EU, and South American governments.
“Last year, we observed different XSS vulnerabilities being used to target additional webmail software: Horde, MDaemon, and Zimbra. Sednit also started to use a more recent vulnerability in Roundcube, CVE-2023-43770. The MDaemon vulnerability — CVE-2024-11182, now patched — was a zero day, most likely discovered by Sednit, while the ones for Horde, Roundcube, and Zimbra were already known and patched,” says ESET researcher Matthieu Faou, who discovered and investigated Operation RoundPress. Sednit sends these XSS exploits by email; the exploits lead to the execution of malicious JavaScript code in the context of the webmail client web page running in a browser window. Therefore, only data accessible from the target’s account can be read and exfiltrated.
In order for the exploit to work, the target must be convinced to open the email message in the vulnerable webmail portal. This means that the email needs to bypass any spam filtering, and the subject line needs to be convincing enough to entice the target into reading the email message — abusing well-known news media such as Ukrainian news outlet Kyiv Post or Bulgarian news portal News.bg. Among the headlines used as spearphishing were: “SBU arrested a banker who worked for enemy military intelligence in Kharkiv” and “Putin seeks Trump’s acceptance of Russian conditions in bilateral relations”.
The attackers unleash JavaScript payloads SpyPress.HORDE, SpyPress.MDAEMON, SpyPress.ROUNDCUBE, and SpyPress.ZIMBRA upon the targets. Those are capable of credential stealing; exfiltration of the address book, contacts, and log-in history; and exfiltration of email messages. SpyPress.MDAEMON is able to set up a bypass for two-factor authentication protection; it exfiltrates the two-factor authentication secret and creates an app password, which enables the attackers to access the mailbox from a mail application.
“Over the past two years, webmail servers such as Roundcube and Zimbra have been a major target for several espionage groups, including Sednit, GreenCube, and Winter Vivern. Because many organizations don’t keep their webmail servers up to date, and because the vulnerabilities can be triggered remotely by sending an email message, it is very convenient for attackers to target such servers for email theft,” explains Faou.
The Sednit group — also known as APT28, Fancy Bear, Forest Blizzard, or Sofacy — has been operating since at least 2004. The U.S. Department of Justice named the group as one of those responsible for the Democratic National Committee (DNC) hack just before the 2016 U.S. elections and linked the group to the GRU. The group is also presumed to be behind the hacking of global television network TV5Monde, the World Anti-Doping Agency (WADA) email leak, and many other incidents.
For a more detailed analysis and technical breakdown of Sednit’s tools used in Operation RoundPress, check out the latest ESET Research blogpost “Operation RoundPress” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X), BlueSky, and Mastodon for the latest news from ESET Research.
Map of operation RoundPress targets, according to ESET telemetry
About ESET
ESET® provides cutting-edge digital security to prevent attacks before they happen. By combining the power of AI and human expertise, ESET stays ahead of emerging global cyberthreats, both known and unknown — securing businesses, critical infrastructure, and individuals. Whether it’s endpoint, cloud, or mobile protection, our AI-native, cloud-first solutions and services remain highly effective and easy to use. ESET technology includes robust detection and response, ultra-secure encryption, and multifactor authentication. With 24/7 real-time defense and strong local support, we keep users safe and businesses running without interruption. The ever-evolving digital landscape demands a progressive approach to security: ESET is committed to world-class research and powerful threat intelligence, backed by R&D centers and a strong global partner network. For more information, visit www.eset.com or follow our social media, podcasts and blogs.
A photo accompanying this announcement is available at https://www.globenewswire.com/NewsRoom/AttachmentNg/eee3ee68-80dc-4136-a11d-6f498092f7d1

Wall St Business News, Latest and Up-to-date Business Stories from Newsmakers of Tomorrow



